tcache-poisoning在safe-linking
preface
Safe-linking is a security mitigation introduced in modern versions of glibc to protect tcache entries from exploitation, such as tcache poisoning.
In CTF pwn challenges, heap operations are infrequent, so the heap state remains the same as it is locally. In such a scenario, if a heap address leak occurs, safe-linking can be easily bypassed. tcache-poisoning is the powerful technique to get an arbitrary read/write primitive.
calculation
Rather than storing the pointer to the next tcache entry in plaintext, glibc obscures it using a simple XOR-based transformation. The idea is to make it harder for an attacker to predict or forge valid pointers. The transformation is defined by the macro:
Here’s what each part means:
pos: This is the address where the current tcache entry is stored.
ptr: This is the actual pointer that we want to protect (usually the next pointer in the linked list).
(size_t) pos >> 12: Shifting the address pos right by 12 bits extracts some of the higher-order bits of the address.
XOR Operation (^): The extracted bits are then XORed with the original pointer. This operation “protects” the pointer, meaning that the stored value is not the real pointer but a transformed version.
An example of calculation
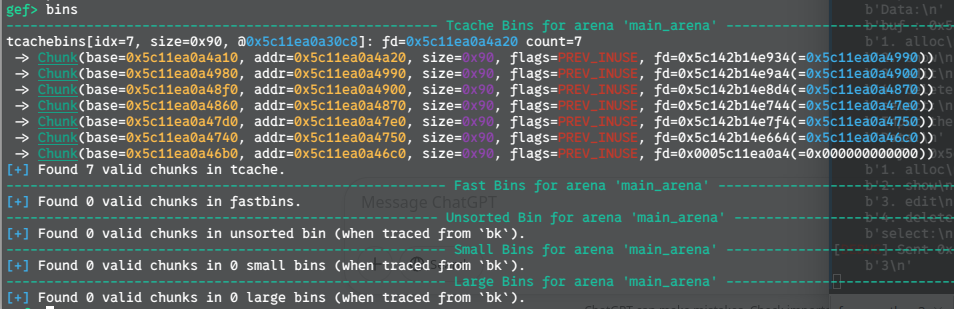
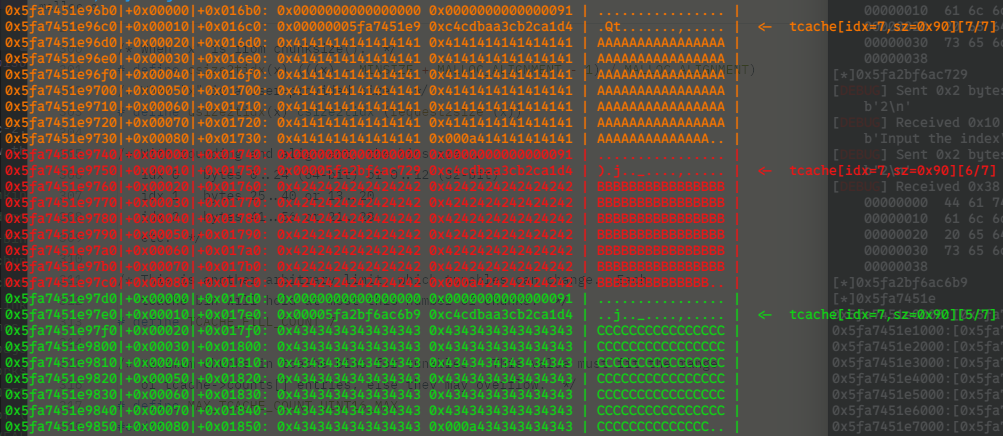
Consider two tcache bin entries for the 0x90-size bin (tcache index 7):
Focus on the pointer at address 0x5fa7451e97e0, which stores the safe-linked value 0x00005fa2bf6ac6b9. According to our macro, this value should be computed as:
tcache-poisoning
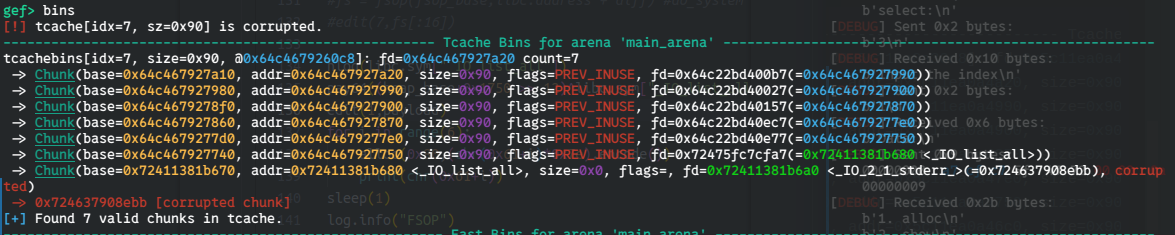
For example, by rewriting the next pointer of the chunk at heap_base as shown below, you can force malloc to allocate memory at the location of _IO_list_all.
When we apply this change, the last bin in the tcache will point to libc’s _IO_list_all, as shown in the picture.