Reverse Engineering
packer
This Challenge Elf is reduced the size of a binary.
Reverse it with 'upx -d'
Check assembly.
I often use Cutter when I want to check assembly.
Then set the breakpoint at before call comp function : 0x4010d0
Run with gdb and check the value of RSI Register.
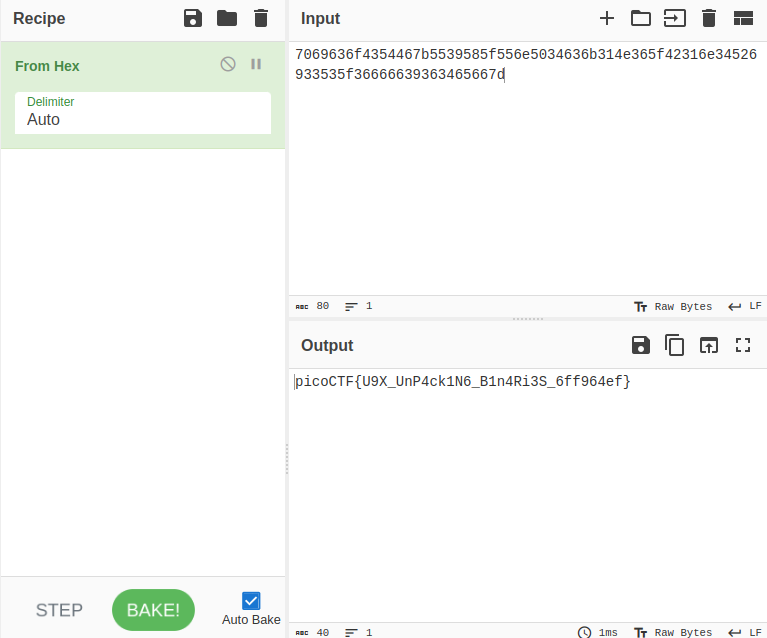
It's a flag in hex.
FactCheck
This Challenge Elf looks operate strings.
It's tiresome to analyze flow of that so set the breakpoint after operate strings.

Debug it with Cutter.
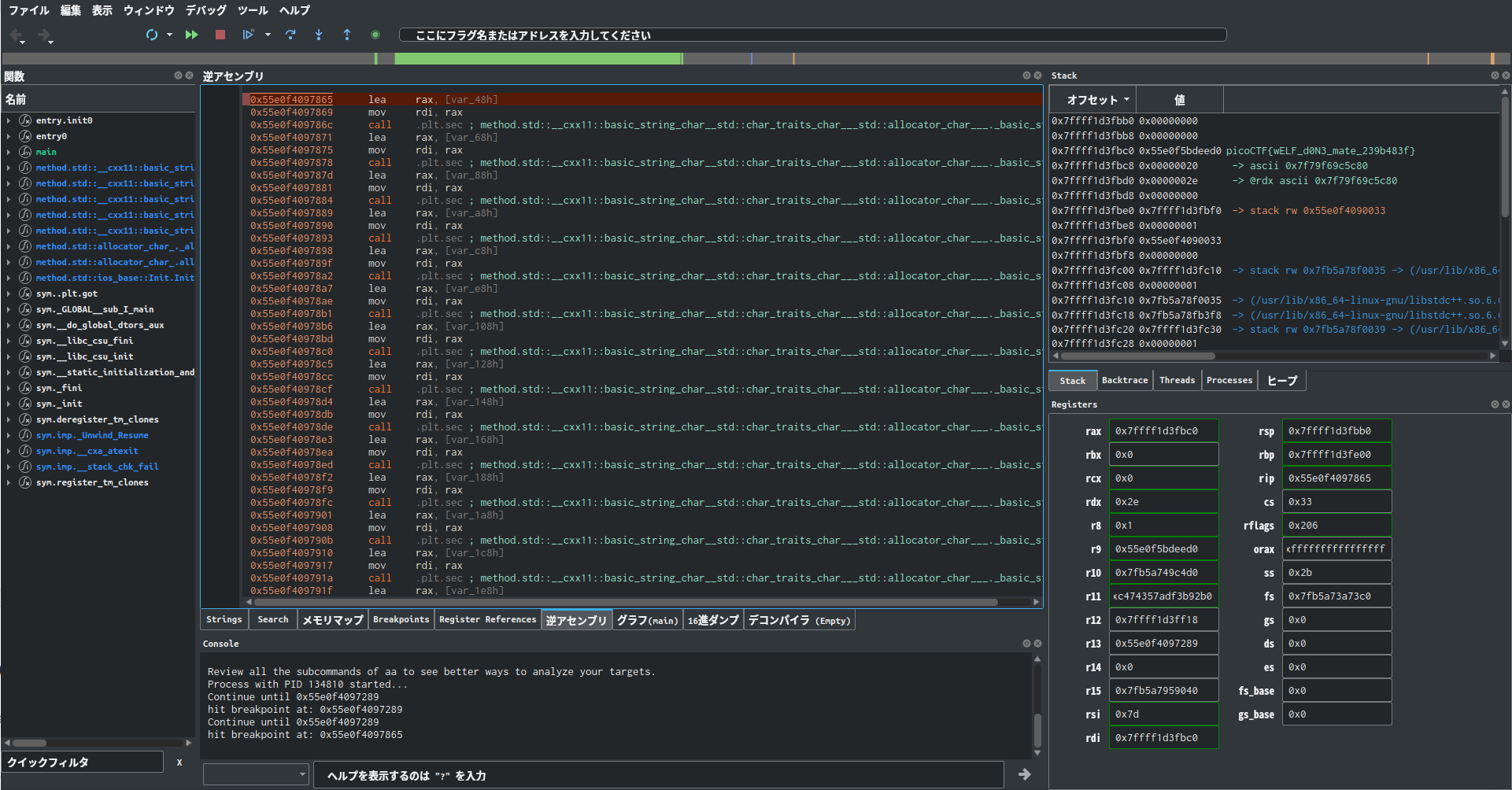
I got the flag in the stack.
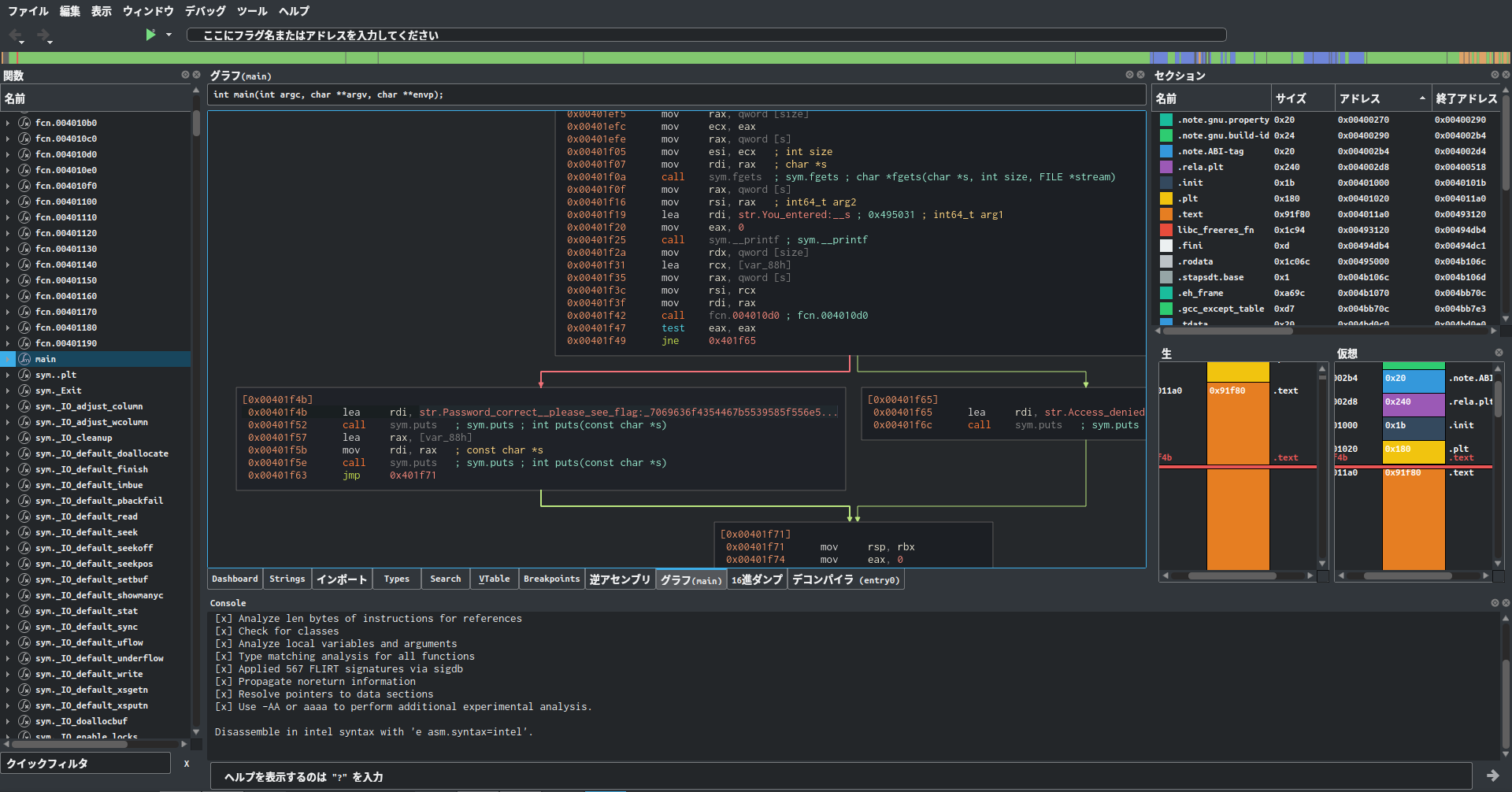
Classic CrackMe 0x100
It's simple auth program.
Decompile it by Ghidra and check main function.
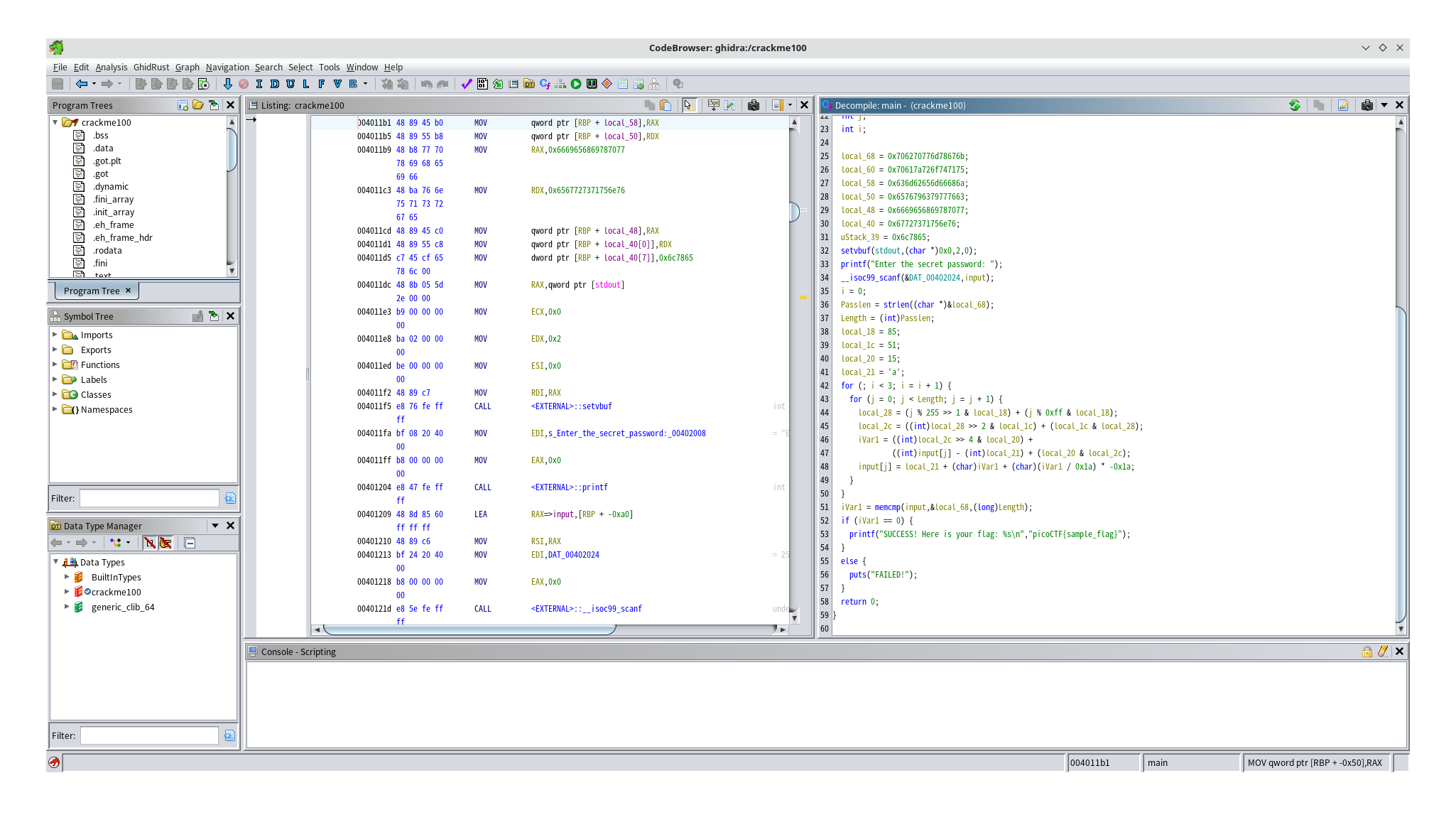
It's makes my input encrypted.
First check the correct encrypted value.
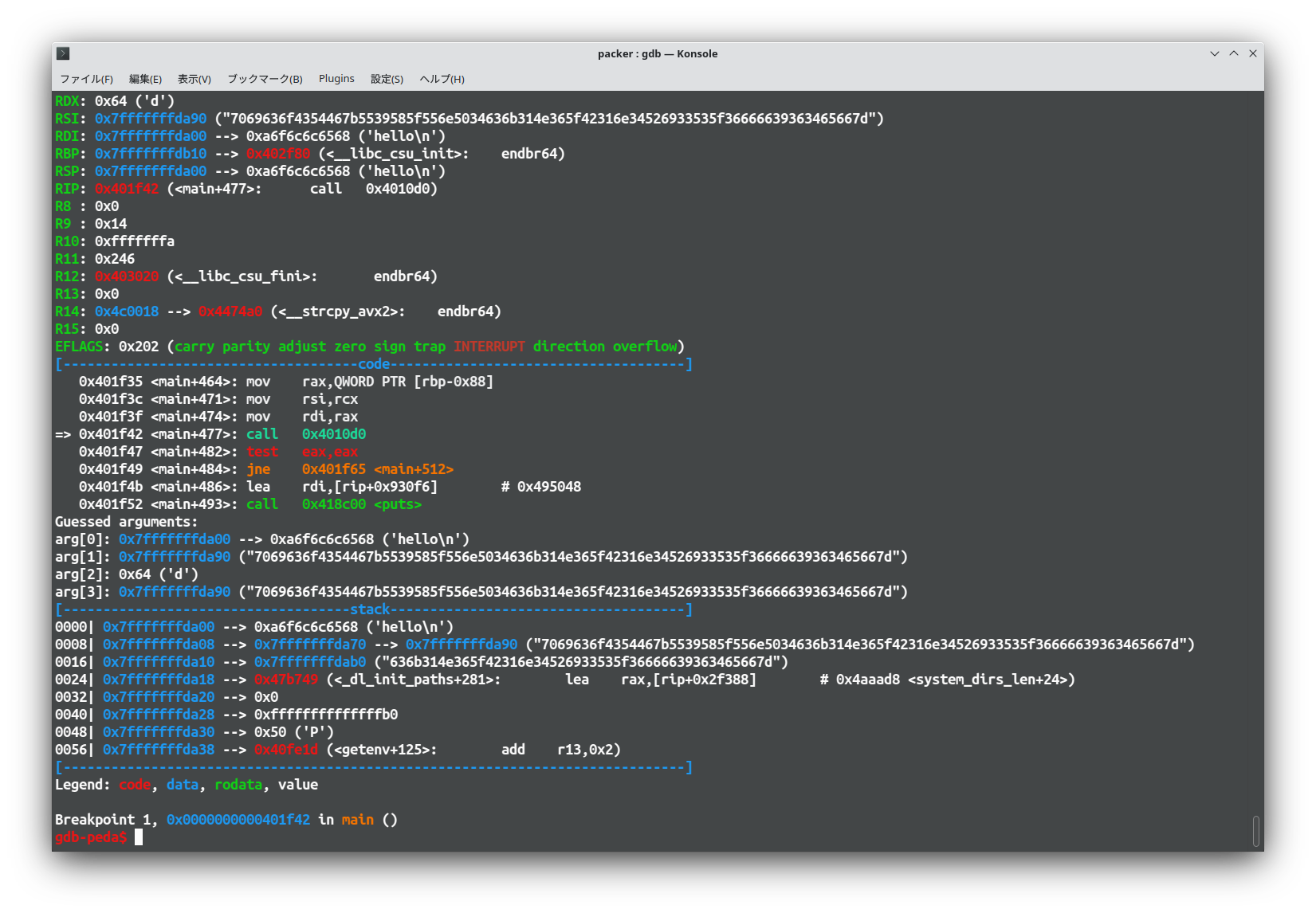
Check the assembly and set breakpoint before memcpy.
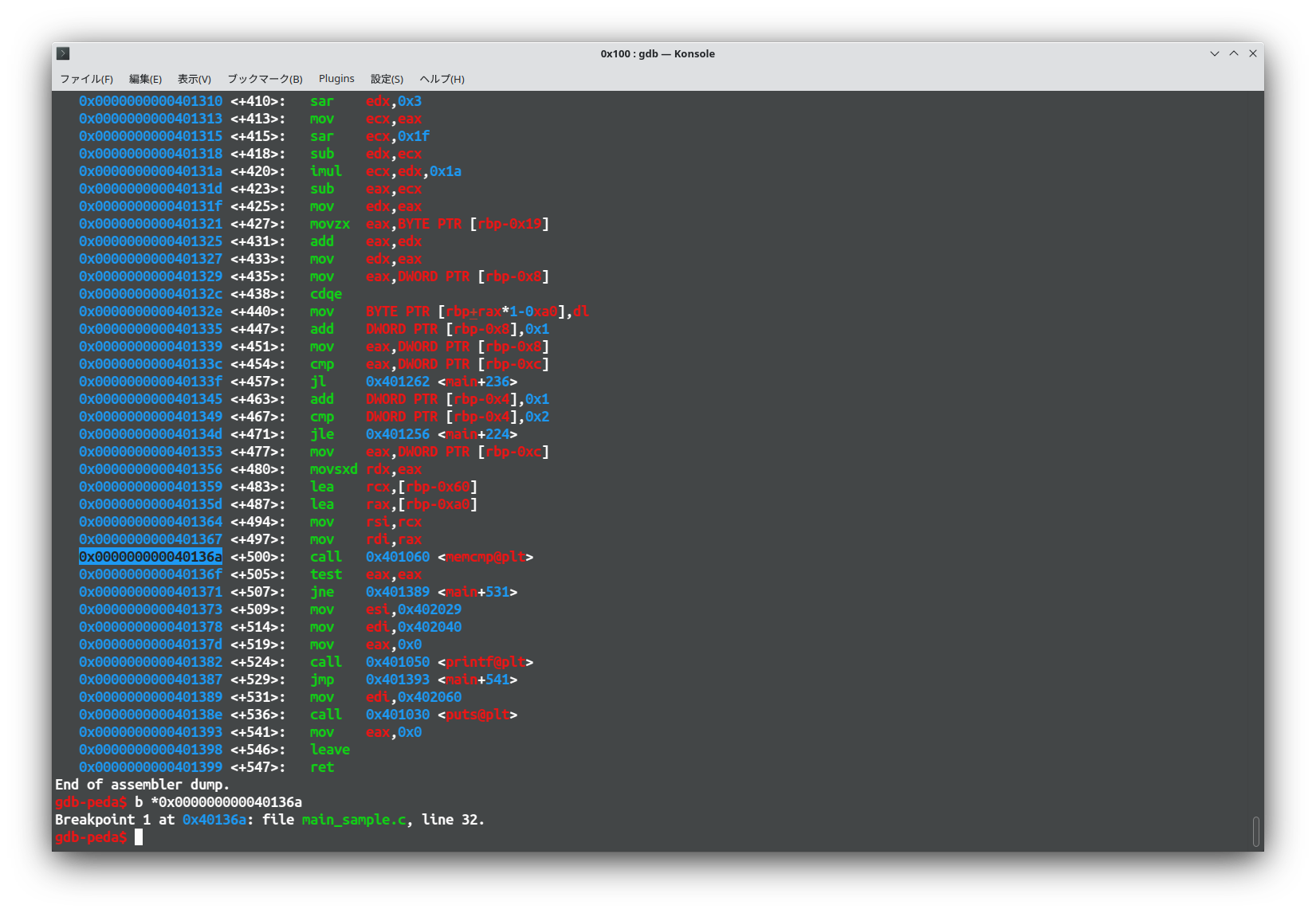
Then run and check RSI register.

Now I have all the value I need to break the encryption.
It's not demanding computation, so I solve it by brute force.
WinAntiDebug 0x100
This challenge needs bypassing Windows Anti Debug.
The challenge file detect if debugger is present or not by calling kernel32.dll::IsDebuggerPresent.
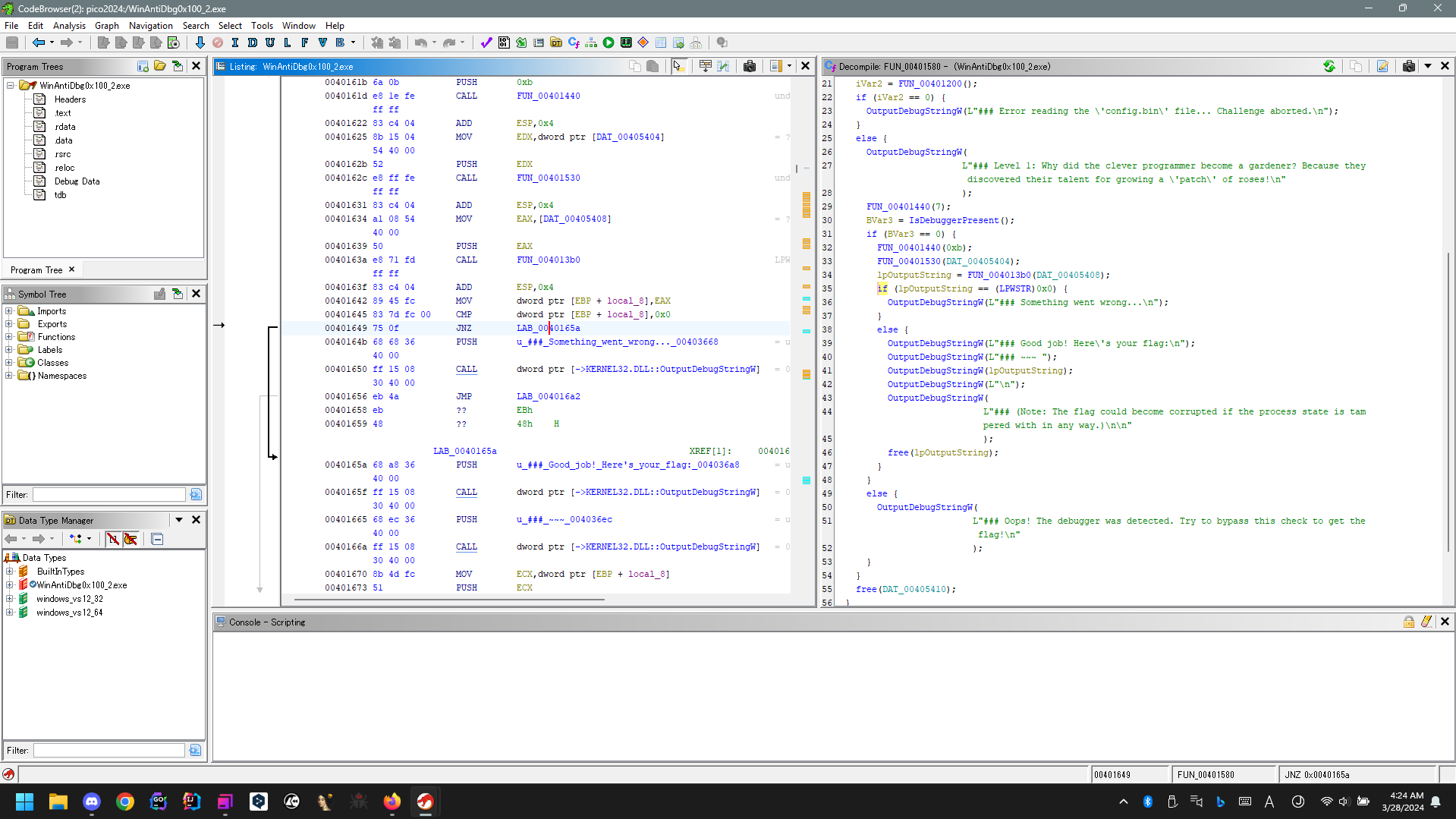
To bypass the debugger presenting, just change return address that exists after detect debugger.
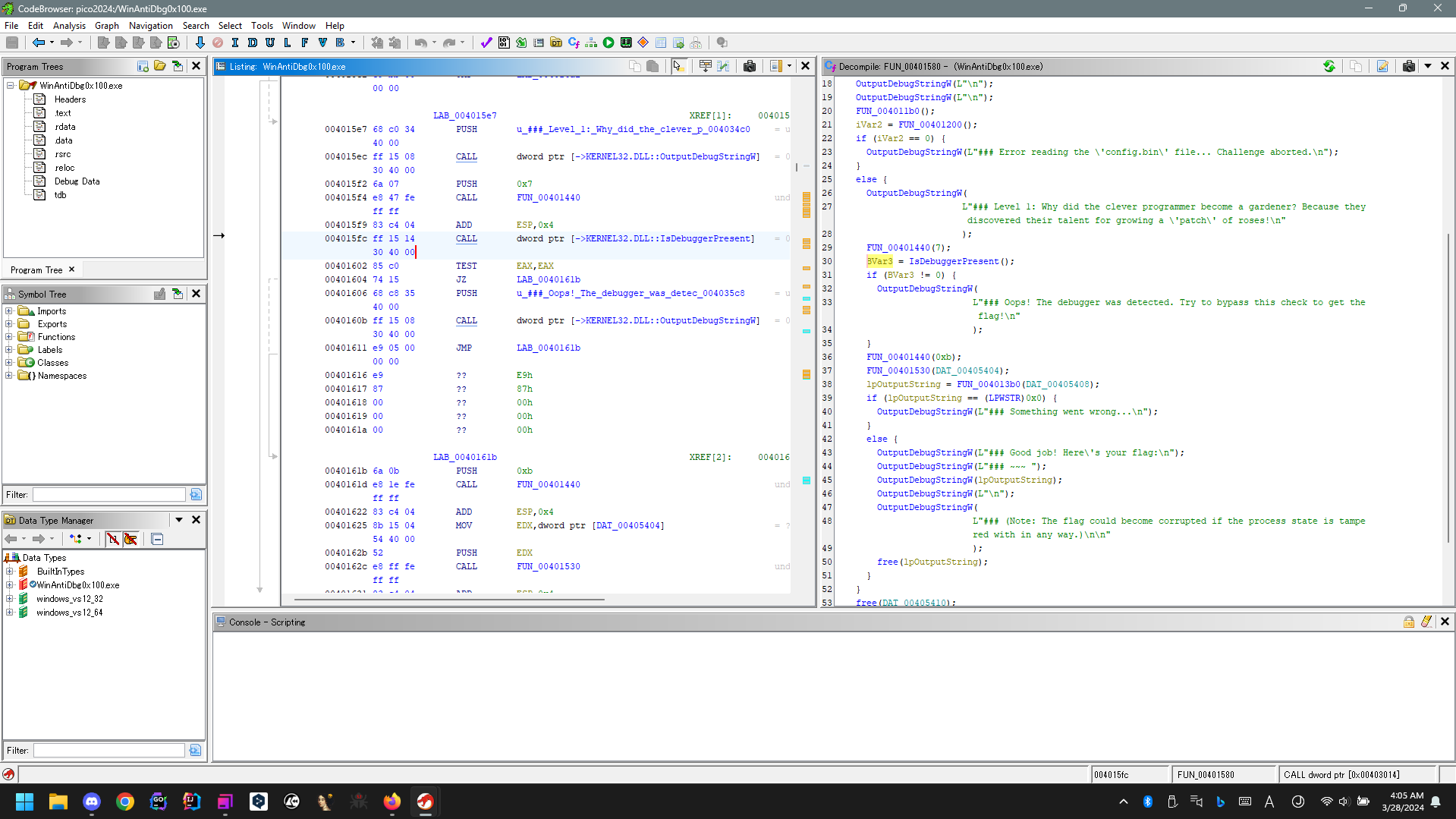
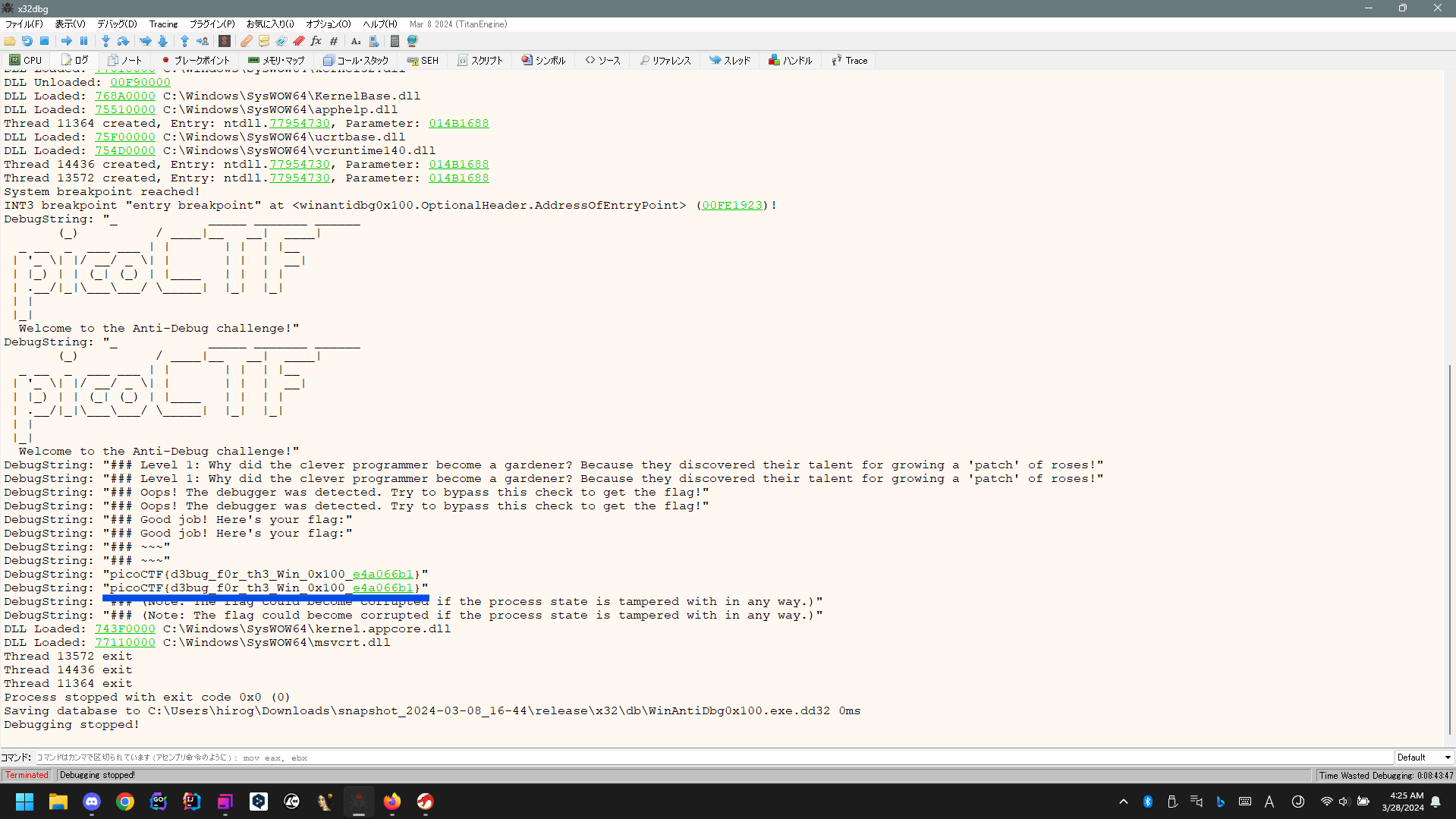
Debug with x32dbg
WinAntiDebug 0x200
This challenge is similar to WinAntiDebug 0x100.
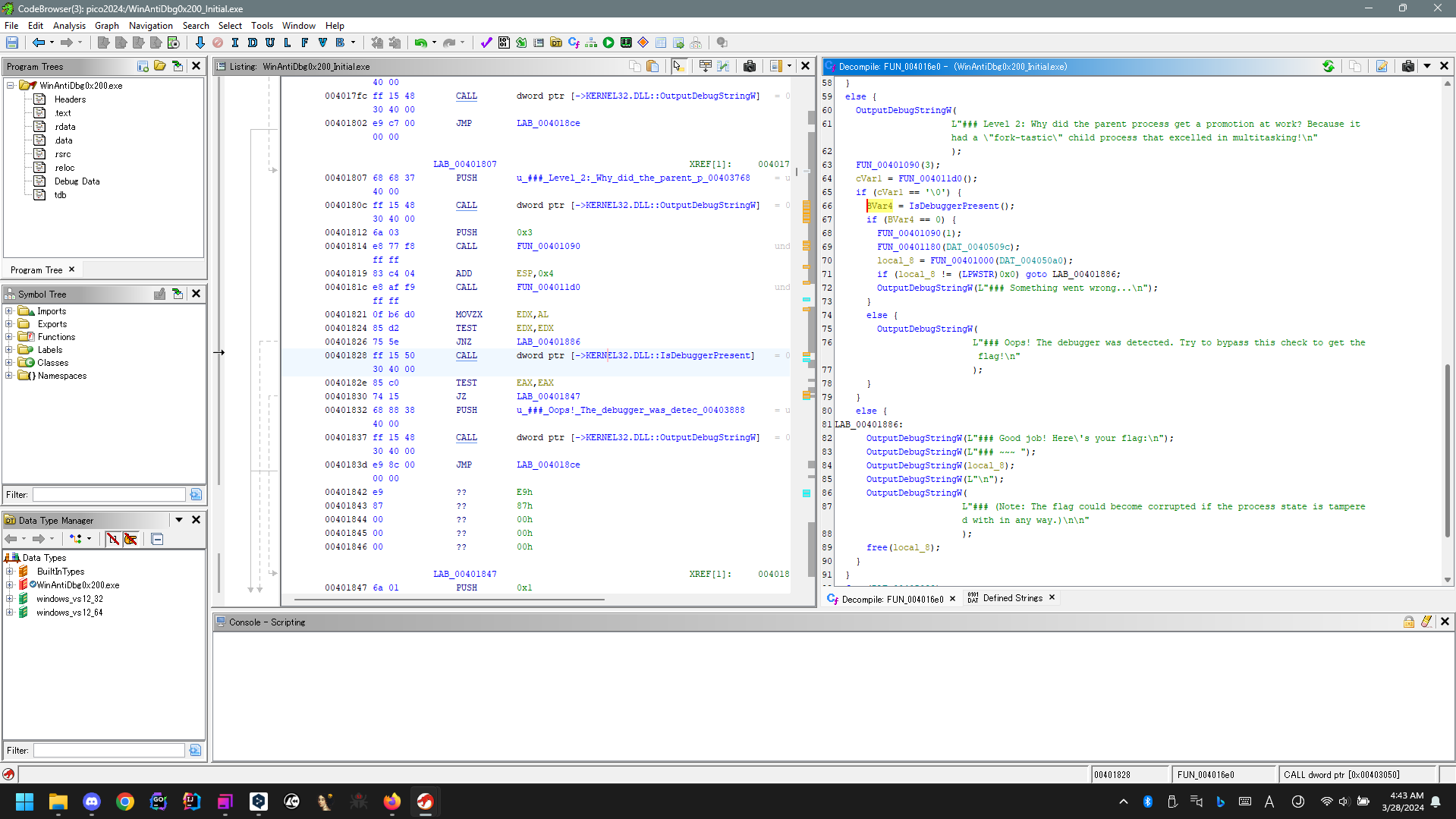
Change the condition of the result of kernel32.dll::IsDebuggerPresent
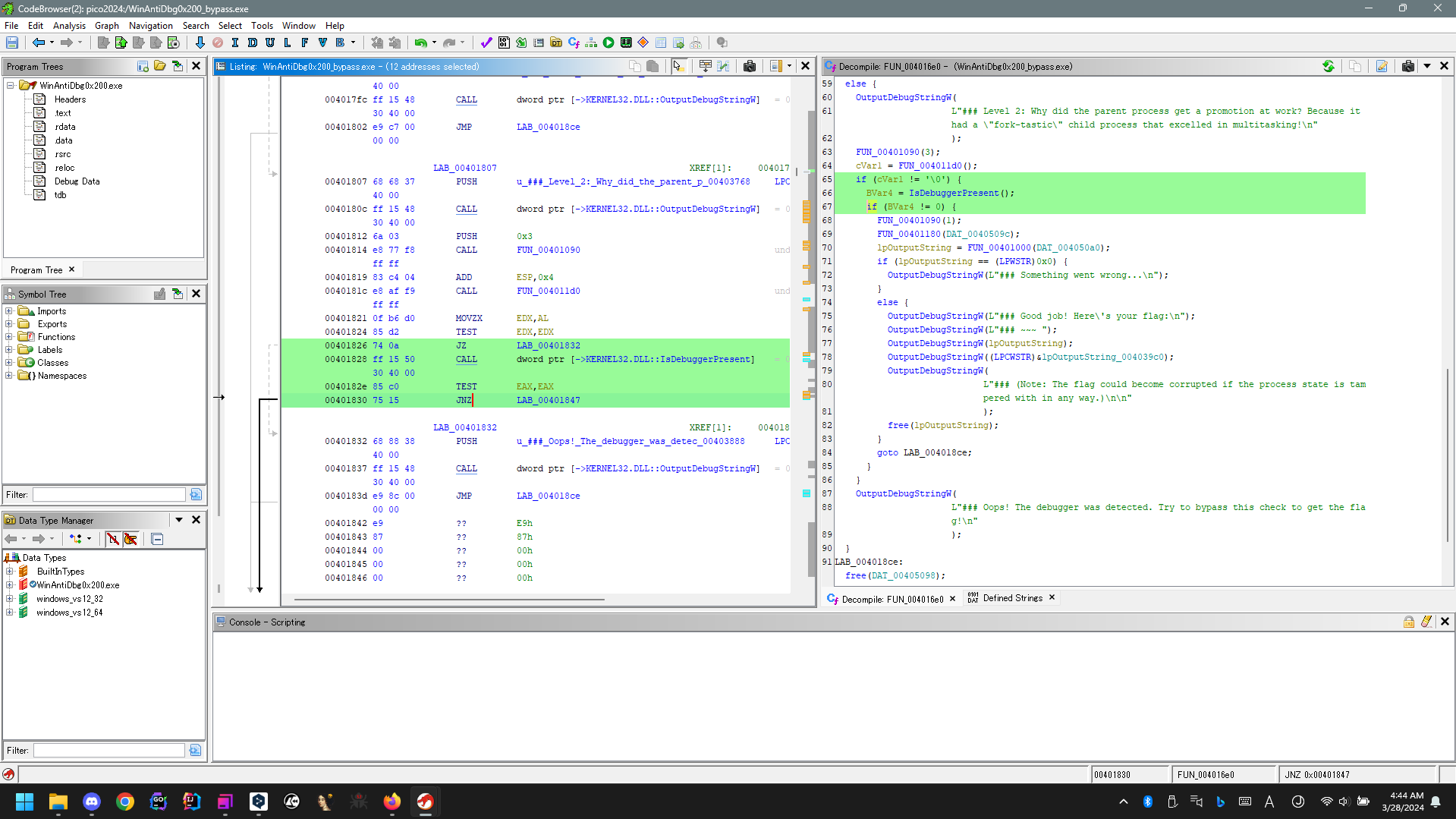
Debug with x32dbg (required administer)