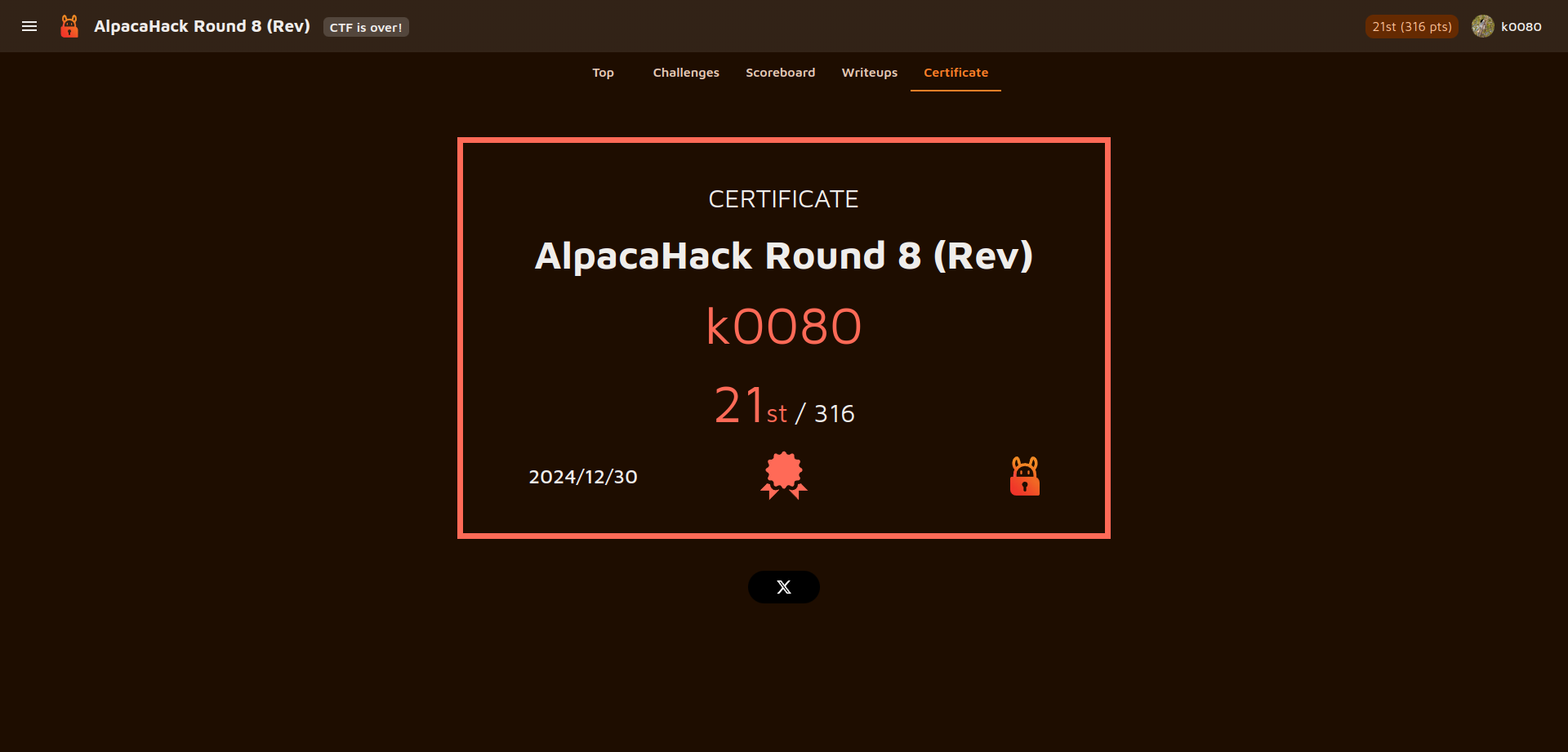
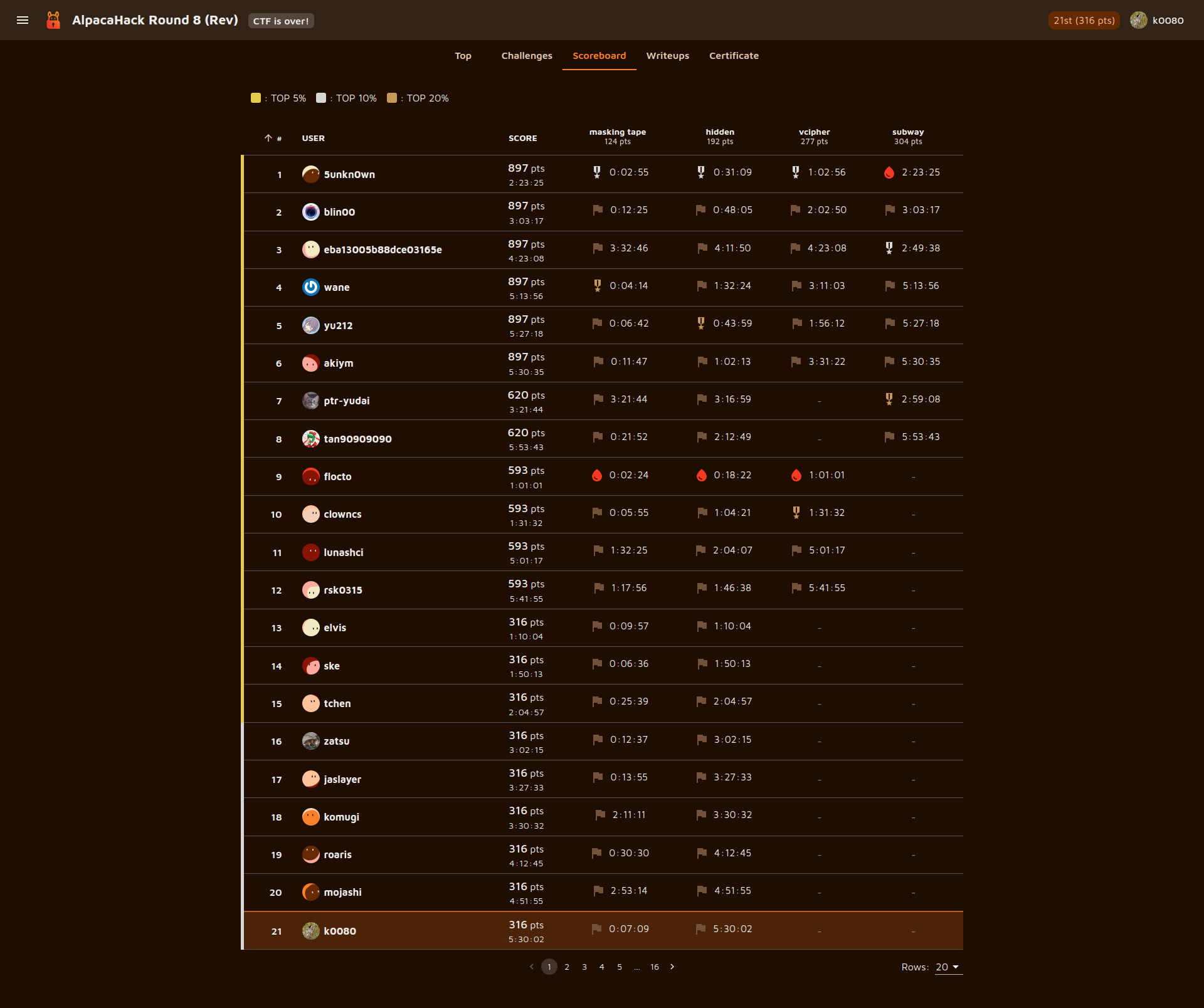
AlpacaHack Round8
Preface
AlpacaHack Round8: https://alpacahack.com/ctfs/round-8 :::info
quote
Welcome to AlpacaHack Round 8 (Rev)! AlpacaHack is a new platform that hosts individual CTF competitions.
AlpacaHack Round 8 is the 8th CTF hosted by the AlpacaHack team, featuring 4 Rev challenges. The challenges are designed with a wide range of difficulties, making them enjoyable for participants of all levels, including beginners. These challenges are created by arata-nvm and sugi! ::: I'd like to thankful for all auther who create funtastic challenges.
masking tape
:::info 124 pts (61 solves) Rev Author: arata-nvm Masking tape is also useful for flag checking :) :::
analysis1
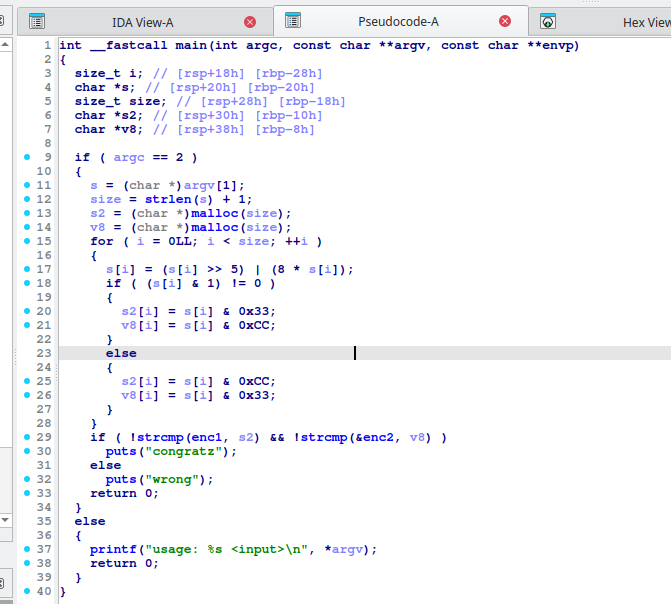
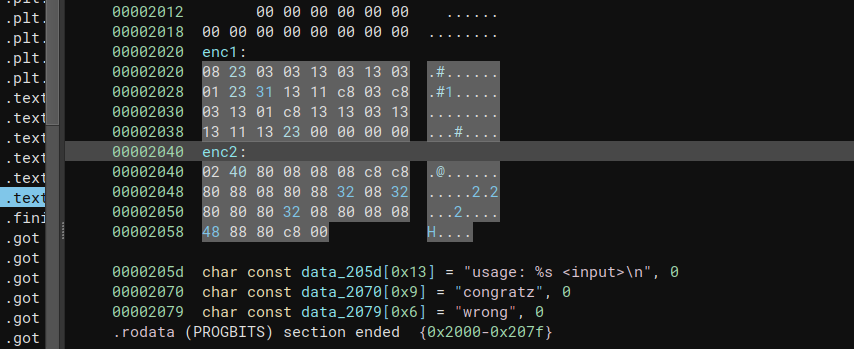
Depending on the state of the least significant bit, either the upper bits or lower bits of the flag are assigned to s2 and v8. Therefore, by performing an OR operation on the values of s2 and v8, the original value can be retrieved. By brute-forcing each character, the flag was successfully obtained. The value of enc1 and enc2 is following.
solver1
hidden
:::info 192 pts (23 solves) Rev Author: arata-nvm How do I hide from a decompiler? :::
Analysis2
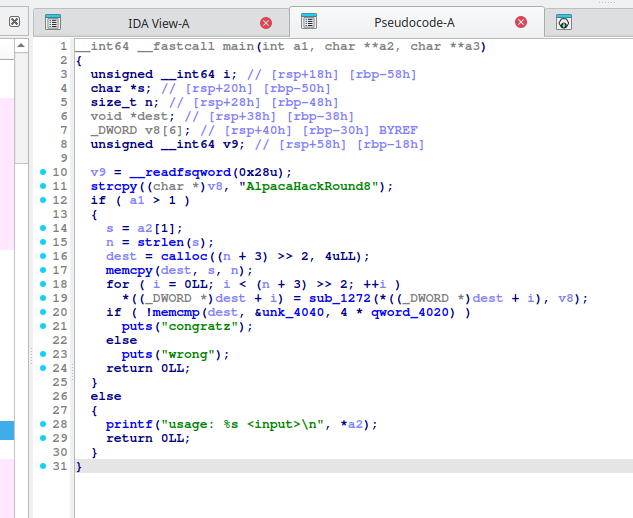
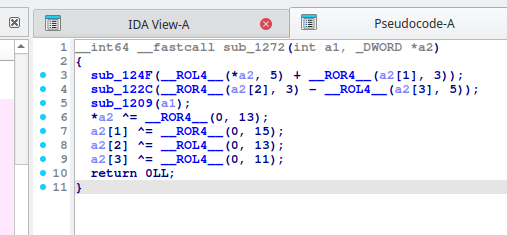
According to the ida, each loop converts three characters of my input string. Given that multiple characters are being transformed and instructions like ROL and ROR are involved, I determined that it would be challenging to reverse the modified correct data mathematically. Since the flag format is Alpaca{}, and I already know the beginning of the flag, brute-forcing the characters was found to be a practical approach to retrieve the flag. By setting a breakpoint at memcmp@plt, I observed that rdi contains the converted input, while rsi contains the correct data. Comparing the memory pointed to by rdi and rsi byte by byte allowed me to identify the flag one character at a time. Using a gdb script to automate debug, I successfully retrieved the flag. However, this solver was quite slow, taking approximately 10 minutes on my computer to find the flag. I'm looking forward to exploring other solutions!
solver2
result