acsc 2025
byte challenge
stage 1
jz short loc_14BA-> jnz short loc_14BA

stage 2
jnz short loc_1548-> jz short loc_1548

stage 3
jz short loc_15FB-> jz short loc_15FB

stage 4
mov rsi, rax-> mov rsi, rbp

solver 1
omit.
book manager
heap overflow @ sub_40191d
int sub_40191D()
{
int v1; // [rsp+8h] [rbp-8h] BYREF
unsigned int v2; // [rsp+Ch] [rbp-4h] BYREF
printf("Book Index: ");
__isoc99_scanf("%d", &v2);
if ( v2 > 0xA || !qword_4040C0[v2] )
return puts("Invalid Index!");
sub_401373(1);
printf("Which Info?: ");
__isoc99_scanf("%d", &v1);
printf("Your Data: ");
if ( v1 > 4 )
return puts("Invalid Option!");
if ( v1 > 2 )
return __isoc99_scanf("%s", *(_QWORD *)(8LL * v1 - 8 + qword_4040C0[v2]));// pwn point
return __isoc99_scanf("%lld", 8LL * v1 - 8 + qword_4040C0[v2]);
}
overwriting string pointer to .got.plt
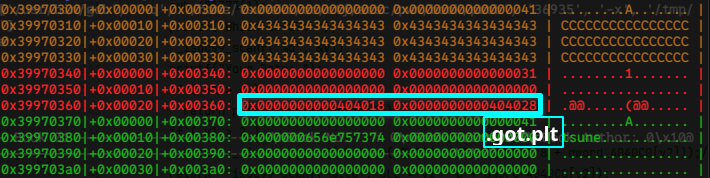
leaking libc address from 0x0000000000404028, falsifying puts@got.plt, puts("/bin/sh") to win a shell.
free | 0x0000004010b0 | 0x000000404018 | 0x7f633f364290 <system>
puts | 0x0000004010c0 | 0x000000404020 | 0x7f633f364290 <system>
printf | 0x0000004010d0 | 0x000000404028 | 0x7f633f373c90 <printf>
memset | 0x0000004010e0 | 0x000000404030 | 0x7f633f49dd30
read | 0x0000004010f0 | 0x000000404038 | 0x7f633f4201e0 <read>
malloc | 0x000000401100 | 0x000000404040 | 0x7f633f3ac0e0 <malloc>
setvbuf | 0x000000401110 | 0x000000404048 | 0x7f633f396ce0 <setvbuf>
__isoc99_scanf | 0x000000401120 | 0x000000404050 | 0x7f633f3750b0 <__isoc99_scanf>
solver 2
omit
Last modified: 26 September 2025